Setup Torrent Tracker Site
How to use Tor for Torrents theres a better option. People often ask, Can Tor be used to download torrents At first glance, this sounds like a great option. Tor has alot of advantages. Xbox 360 Theme Creator Horizon more. First, its free which people love. And second, it uses multiple layers of encrypted proxies, so it should be highly anonymous. All these things are true, and Tor can be used as a torrent proxy. But it shouldnt be, and Im hoping to convince you why. But dont worry, theres a much better alternative for anonymous torrents. Tors only advantage is its cost free, but its not the best tool for the job. Not even close. What is Tor Tor is a free anticensorship tool, designed to help people around the world communicate safely and access content without restrictions. Setup Torrent Tracker Site' title='Setup Torrent Tracker Site' />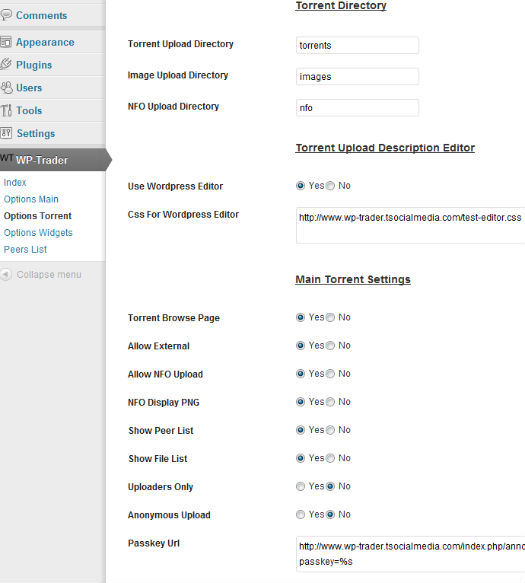 At its core is a series of encrypted proxies, which are routed randomly and layered like an onion. The theory is that if you tunnel your internet traffic through three or more encrypted proxies, the 1st layer will know your identity, the last layer will know your destination, but no one will be able to connect the two. Setup Torrent Tracker Site' title='Setup Torrent Tracker Site' />Check out the best torrent websites 2017, from The Pirate Bay to ExtraTorrent, ISOHunt, and Torrentz2, which rank among the best torrenting sites 2017. Worlds Largest Bitcoin Marketplace with automated escrow. Earn Bitcoin by selling online. Maximizing BitTorrent Speeds with uTorrent Guide Tutorial Version 1. Updated July 2014 This article explains how to get up and running with utorrent. BitTorrent is a leading software company with the fastest torrent client and sync and share software for Mac, Windows, Linux, iOS and Android. Torrentz will always love you. Farewell. 20032016 Torrentz. A 27yearold man had been suffering frequent headaches and had been falling over frequently for around three years. But when he had a seizure, he headed to the. Google Analytics lets you measure your advertising ROI as well as track your Flash, video, and social networking sites and applications. Setup Torrent Tracker Site' title='Setup Torrent Tracker Site' />Millions of BitTorrent downloaders use proxies or VPN services to protect their privacy while downloading. These tools offer anonymity by replacing ones residential. There are many services that promise to hide your IPaddress, but do they also work with your favorite BitTorrent client Luckily, theres now an open source tool. I just released Transdroid 2. It includes bug fixes, such as for the rTorrent file upload restriction, but more importantly it supports the new Torrent Search 2. All Tor proxy nodes are run by volunteers, and the entire network is based on a theory that all Tor node operators are trustworthy which is unlikely. Even so, Tor is still highly secure, and anonymous. Most people access Tor through the Tor Browser bundle, which is a specially configured version of firefox, designed to easily route all traffic through the Tor network. This is great for visiting a website anonymously though you will face constant captchas anti spam challenges. Can Tor be used to Download Torrents
At its core is a series of encrypted proxies, which are routed randomly and layered like an onion. The theory is that if you tunnel your internet traffic through three or more encrypted proxies, the 1st layer will know your identity, the last layer will know your destination, but no one will be able to connect the two. Setup Torrent Tracker Site' title='Setup Torrent Tracker Site' />Check out the best torrent websites 2017, from The Pirate Bay to ExtraTorrent, ISOHunt, and Torrentz2, which rank among the best torrenting sites 2017. Worlds Largest Bitcoin Marketplace with automated escrow. Earn Bitcoin by selling online. Maximizing BitTorrent Speeds with uTorrent Guide Tutorial Version 1. Updated July 2014 This article explains how to get up and running with utorrent. BitTorrent is a leading software company with the fastest torrent client and sync and share software for Mac, Windows, Linux, iOS and Android. Torrentz will always love you. Farewell. 20032016 Torrentz. A 27yearold man had been suffering frequent headaches and had been falling over frequently for around three years. But when he had a seizure, he headed to the. Google Analytics lets you measure your advertising ROI as well as track your Flash, video, and social networking sites and applications. Setup Torrent Tracker Site' title='Setup Torrent Tracker Site' />Millions of BitTorrent downloaders use proxies or VPN services to protect their privacy while downloading. These tools offer anonymity by replacing ones residential. There are many services that promise to hide your IPaddress, but do they also work with your favorite BitTorrent client Luckily, theres now an open source tool. I just released Transdroid 2. It includes bug fixes, such as for the rTorrent file upload restriction, but more importantly it supports the new Torrent Search 2. All Tor proxy nodes are run by volunteers, and the entire network is based on a theory that all Tor node operators are trustworthy which is unlikely. Even so, Tor is still highly secure, and anonymous. Most people access Tor through the Tor Browser bundle, which is a specially configured version of firefox, designed to easily route all traffic through the Tor network. This is great for visiting a website anonymously though you will face constant captchas anti spam challenges. Can Tor be used to Download Torrents The tor network uses layers Socks proxies, so technically any app or software that can connect to a socks proxy can use Tor. This includes things like Skype, Android, and most desktop torrent clients. But before you rush to setup u. Torrent to use Tor, there are a few downsides to consider 1 Tor is designed to enable free speech and fight censorship, not to download MP3s. This assessment may seem harsh, but lets be honest the volunteers that pledge their time, money, and bandwidth to Tor are doing it in an effort to make the world a better, safer place. Not to help you use u. Torrent anonymously. Tors bandwidth is severely limited, so from a human perspective, its important to save that limited bandwidth for those that really need it. People use Tor every day to speak freely against authoritarian, violent governments, or to publish sensitive articlesblogs anonymously. Tor enables people to expose corruption, abuse, and oppression in relative safety. This is incredibly important, and we shouldnt clog the Tor network with high bandwidth torrent traffic, which would could literally overwhelm and break the entire system. Your torrent client can still leak your true IP when using Tor as a proxy. Researchers in France were able to de anonymize over 1. TOR. They were surprised at how easy it was, and in over 23 of the cases, they didnt actually have to do anything to trace a torrent users real IP address. The reason Tor was only being used to connect to the tracker. Peer connections were routed outside Tor. To be clear, this isnt Tors fault. Canon Pixma Mp287 P07 Error Resetter'>Canon Pixma Mp287 P07 Error Resetter. It means the user either had an improperly configured torrent client not setup to proxy peer connections. Alternatively, these peers could have been using a torrent client that doesnt actual support the proxying of peer connections examples include Transmission, Tixati. Tor doesnt support UDP connections like DHT so any non TCP connection can leak your IPDHT Distributed Hash Table has become a core bittorrent technology. Magnet links dont work without it. But theres one problem, DHT relies on the UDP transport protocol, and Tor cant handle UDP connections. Some torrent clients might just disable non supported functions. But most will simply ignore your proxy settings for UDP, and route them outside the Tor tunnel and leak your real IP address to all DHT peers. Yikes Have you ever tried to stream HD video over Tor Its not pretty. Youll be lucky to get 4. HD. If you have a fast connection 1. Tor. Isnt the whole point of torrenting to get content quickly and conveniently Downloads that take all day should be a thing of the past. Tor Alternatives So if Tor isnt a good choice for anonymizing your torrents, what are the other options Well theres two Zero Log VPN service best choice We recommend Private Internet Access. Zero Log Socks. 5 proxy less secure, but can be combined with VPN for maximum flexibility. And dont worry, you dont really have to choose one or the other. There are several VPN providers that actually included a torrent friendly SOCKS5 proxy service at no additional charge included with all subscriptions. A VPN Service Virtual Private Network will route all of your internet traffic through a 3rd party server owned by your VPN service changes your public IP address. All traffic will also be encrypted with extremely strong 1. This provides protection from the two main ways torrents are monitored By your public IP address in torrent swarms they will see your VPN services IP insteadYour ISP monitoring your traffic directly the encryption prevents your internet provider from reading your traffic. Sound X Smi 1458 Manual. Its important that you choose a non logging VPN. If the VPN provider keeps connecition or activity logs, they could voluntarily share your previous connection history what IP addresses you used. If the VPN keeps no logs, this is impossible. Heres how a high quality VPN compares to Tor VPNEncrypts entire internet connection. Control where your exit node is located. Capable of 1. 00mbpsup to 2. AES encryption strength. No settings changed in torrent client software. All torrent connections go through VPN tunnel. Tor. Encryptshides only specific programs. Random exit location where your IP is fromSlow. Mbps is typical 1. AES encryption still strongManual setup required for torrent client. Some torrent connections may be routed insecurely. And most importantly, a VPN service isnt vulnerable to the same Bad Apple attacks the researchers used on Tor users to deanonymize 1. As long as you choose a non logging VPN provider and you trust them, your torrent activity should be nearly 1. So far, Private Internet Access is the only VPN whos non logging claims have been tested in court they passed. PIA refused to hand over IP evidence to the FBI, stating that they didnt have any records or logs to hand over. Thats the closest thing to a 1. Get a 1 year unlimited PIA subscription for 3. How do you use a VPN for torrentsThere is no complicated setup required to torrent anonymously with a VPN. Simply download your VPN providers software on your device most have a custom app for WindowsMaci. OSAndroid. Then just choose a server location we recommend the Netherlands. Click Connect and youre good to goOn this site, we also recommend using a zero log Socks. It will change your torrent IP address and give you nearly 1. ISP assigned speeds. The downside is using a proxy to anonymize your torrents requires manual setup in your torrent client of choice. Also, some torrent clients will route peer connections outside the proxy tunnel bad. But how does Tor compare to Socks. Well, Tor is actually a network of layered Socks. So instead of using a single proxy server, Tor will route your traffic through 3 proxies, with 1. Its far more anonymous than 1 Socks proxy, much MUCH slower. The main advantage of Tor vs.
The tor network uses layers Socks proxies, so technically any app or software that can connect to a socks proxy can use Tor. This includes things like Skype, Android, and most desktop torrent clients. But before you rush to setup u. Torrent to use Tor, there are a few downsides to consider 1 Tor is designed to enable free speech and fight censorship, not to download MP3s. This assessment may seem harsh, but lets be honest the volunteers that pledge their time, money, and bandwidth to Tor are doing it in an effort to make the world a better, safer place. Not to help you use u. Torrent anonymously. Tors bandwidth is severely limited, so from a human perspective, its important to save that limited bandwidth for those that really need it. People use Tor every day to speak freely against authoritarian, violent governments, or to publish sensitive articlesblogs anonymously. Tor enables people to expose corruption, abuse, and oppression in relative safety. This is incredibly important, and we shouldnt clog the Tor network with high bandwidth torrent traffic, which would could literally overwhelm and break the entire system. Your torrent client can still leak your true IP when using Tor as a proxy. Researchers in France were able to de anonymize over 1. TOR. They were surprised at how easy it was, and in over 23 of the cases, they didnt actually have to do anything to trace a torrent users real IP address. The reason Tor was only being used to connect to the tracker. Peer connections were routed outside Tor. To be clear, this isnt Tors fault. Canon Pixma Mp287 P07 Error Resetter'>Canon Pixma Mp287 P07 Error Resetter. It means the user either had an improperly configured torrent client not setup to proxy peer connections. Alternatively, these peers could have been using a torrent client that doesnt actual support the proxying of peer connections examples include Transmission, Tixati. Tor doesnt support UDP connections like DHT so any non TCP connection can leak your IPDHT Distributed Hash Table has become a core bittorrent technology. Magnet links dont work without it. But theres one problem, DHT relies on the UDP transport protocol, and Tor cant handle UDP connections. Some torrent clients might just disable non supported functions. But most will simply ignore your proxy settings for UDP, and route them outside the Tor tunnel and leak your real IP address to all DHT peers. Yikes Have you ever tried to stream HD video over Tor Its not pretty. Youll be lucky to get 4. HD. If you have a fast connection 1. Tor. Isnt the whole point of torrenting to get content quickly and conveniently Downloads that take all day should be a thing of the past. Tor Alternatives So if Tor isnt a good choice for anonymizing your torrents, what are the other options Well theres two Zero Log VPN service best choice We recommend Private Internet Access. Zero Log Socks. 5 proxy less secure, but can be combined with VPN for maximum flexibility. And dont worry, you dont really have to choose one or the other. There are several VPN providers that actually included a torrent friendly SOCKS5 proxy service at no additional charge included with all subscriptions. A VPN Service Virtual Private Network will route all of your internet traffic through a 3rd party server owned by your VPN service changes your public IP address. All traffic will also be encrypted with extremely strong 1. This provides protection from the two main ways torrents are monitored By your public IP address in torrent swarms they will see your VPN services IP insteadYour ISP monitoring your traffic directly the encryption prevents your internet provider from reading your traffic. Sound X Smi 1458 Manual. Its important that you choose a non logging VPN. If the VPN provider keeps connecition or activity logs, they could voluntarily share your previous connection history what IP addresses you used. If the VPN keeps no logs, this is impossible. Heres how a high quality VPN compares to Tor VPNEncrypts entire internet connection. Control where your exit node is located. Capable of 1. 00mbpsup to 2. AES encryption strength. No settings changed in torrent client software. All torrent connections go through VPN tunnel. Tor. Encryptshides only specific programs. Random exit location where your IP is fromSlow. Mbps is typical 1. AES encryption still strongManual setup required for torrent client. Some torrent connections may be routed insecurely. And most importantly, a VPN service isnt vulnerable to the same Bad Apple attacks the researchers used on Tor users to deanonymize 1. As long as you choose a non logging VPN provider and you trust them, your torrent activity should be nearly 1. So far, Private Internet Access is the only VPN whos non logging claims have been tested in court they passed. PIA refused to hand over IP evidence to the FBI, stating that they didnt have any records or logs to hand over. Thats the closest thing to a 1. Get a 1 year unlimited PIA subscription for 3. How do you use a VPN for torrentsThere is no complicated setup required to torrent anonymously with a VPN. Simply download your VPN providers software on your device most have a custom app for WindowsMaci. OSAndroid. Then just choose a server location we recommend the Netherlands. Click Connect and youre good to goOn this site, we also recommend using a zero log Socks. It will change your torrent IP address and give you nearly 1. ISP assigned speeds. The downside is using a proxy to anonymize your torrents requires manual setup in your torrent client of choice. Also, some torrent clients will route peer connections outside the proxy tunnel bad. But how does Tor compare to Socks. Well, Tor is actually a network of layered Socks. So instead of using a single proxy server, Tor will route your traffic through 3 proxies, with 1. Its far more anonymous than 1 Socks proxy, much MUCH slower. The main advantage of Tor vs.